How to Secure Wan Networks from Malicious Attacks?
Published: January 22, 2025
A Wide area network (WAN) connects devices over large distances, such as by linking different office locations of a company. It allows employees and systems to communicate and share data in other cities or countries.
While WANs are essential for businesses, they are also attractive targets for hackers. Why? WANs carry important and sensitive data, such as customer details, financial records, or confidential business information. Hackers try to exploit these networks using methods like Phishing, Malware, and Denial of Service (DoS) Attacks.
This is why securing a WAN is critical to protect your business and data from these risks.
To protect your WAN, you need to implement strong security measures. This guide will help you understand common threats and how to safeguard your network.
Understanding the Threats
Malicious attacks on WANs can cause severe damage. Here are some common threats:
1. Phishing
Hackers trick employees into revealing sensitive information, such as passwords.
2. Denial of Service (DoS)
Overloading the network with fake traffic to disrupt services.
3. Malware/Ransomware
Infecting systems to steal, encrypt, or destroy data until a ransom is paid.
4. Man-in-the-Middle (MITM)
Hackers intercept data as it travels across the network, stealing or altering it.
Understanding these risks is the first step in securing your WAN.
Importance of Securing WAN Networks
Failing to secure your WAN can lead to:
- Data breaches expose sensitive information like customer data or financial records.
- System downtime, halting operations, and reducing productivity.
- Reputational damage causes a loss of trust among customers and partners.
- By addressing these vulnerabilities, you protect your business, reputation, and bottom line.
Key Measures to Secure a WAN
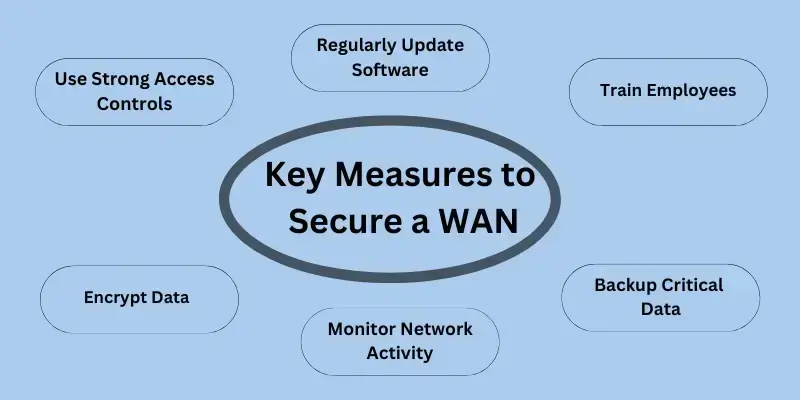
Step 1: Use Strong Access Controls
Set up firewalls to block unauthorized access.
Implement Role-Based Access Control (RBAC), ensuring employees only access what they need.
Use strong passwords and enable multi-factor authentication (MFA) to add an extra layer of security.
Step 2: Encrypt Data
Encrypting data during transmission prevents hackers from reading it, even if intercepted. Use protocols like IPSec or TLS for secure communication.
Step 3: Regularly Update Software
Software updates fix security flaws. Keep operating systems, firmware, and applications up-to-date to prevent attacks exploiting old vulnerabilities.
Step 4: Monitor Network Activity
Deploy tools like Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) to identify and block suspicious behavior. For example, if a device suddenly sends an unusually high volume of data, these tools can alert you.
Step 5: Train Employees
Employees are often the weakest link. Educate them about:
- Recognizing phishing attempts.
- Avoiding unverified links or downloads.
- Reporting unusual activity immediately.
Step 6: Backup Critical Data
Backups ensure your business can recover from attacks. Store backups in secure locations, test them regularly and consider using both on-site and cloud solutions.
Tips for Small Businesses and Beginners
Small businesses can start with simple, cost-effective measures:
- Use a VPN for secure remote access.
- Invest in essential security software for endpoints (antivirus and firewalls).
- Outsource security to managed services if internal expertise is limited.
Conclusion
Securing a WAN is not a one-time task—it’s an ongoing process. Implementing strong access controls, encrypting data, monitoring activity, and training employees can greatly reduce the risk of malicious attacks.
Take action today: Review your current security setup and address any weak spots. Remember, in cybersecurity, prevention is always better than cure.
FAQs About How to Secure Wan Networks from Malicious Attacks?
Common attacks include phishing (stealing passwords through fake emails), malware (infecting systems to steal or lock data), and Denial of Service (DoS) (overloading the network to disrupt services). These can cause data loss, downtime, and financial damage.
Start by using firewalls, strong passwords, and multi-factor authentication. Then, update software regularly, encrypt data, and monitor network activity for unusual behavior.
A VPN helps secure remote connections by encrypting data, but it’s insufficient. For comprehensive protection, pair it with firewalls, monitoring tools, and regular security updates.
Look for signs like unusually slow performance, unexpected system crashes, or alerts from security tools. Intrusion Detection Systems (IDS) can also help identify suspicious activities.
You should update your security software and tools as soon as updates are available. Additionally, conduct a full security audit every 3–6 months to ensure your defenses are up to date.
Provide simple training sessions on recognizing phishing emails, avoiding suspicious links, and using strong passwords. Encourage employees to report anything unusual immediately.
Small businesses can use cost-effective tools like VPNs, antivirus software, and basic firewalls. Managed security services can also provide professional support at reasonable rates.
Encryption converts data into unreadable code during transmission, so even if hackers intercept it, they can’t understand it. Tools like IPSec or TLS ensure secure communication across your WAN.
Disconnect affected systems immediately to stop the attack from spreading. Notify your IT team, investigate the breach, and restore data from secure backups. Strengthen your defenses to prevent future attacks.
WAN options for small businesses include MPLS (Multiprotocol Label Switching), VPNs (Virtual Private Networks), and SD-WAN (Software-Defined WAN) to connect remote offices securely. MPLS offers reliable, dedicated connections, while VPNs are cost-effective for secure data transmission. SD-WAN provides flexibility, improves performance, and reduces costs.
How can the TCP/IP model secure WAN networks from malicious attacks?
To secure WAN networks, TCP/IP security measures like encryption, firewalls, VPNs, and intrusion detection systems (IDS) protect data, ensure secure routing, and prevent unauthorized access.
Secure, high-quality backbone cables can enhance WAN reliability, making it harder for malicious attacks to disrupt communication or steal sensitive data.